起因 自从用上了VPS,爆破ssh端口的小黑们就一刻也没挺过,虽然我仍然使用的密码登录,自认为自己设置的密码还是足够的强健,但是还是想记录一下他们爆破所用的字典。搜索了几种方式,例如可以使用蜜罐,更改openssh源码等方式来记录爆破字典。为了省事,我采用了修改源码的方式来进行记录。
步骤1 搭建编译环境 我所使用的环境是CentOS 7,需要安装openssl-devel和pam-devel
1 root@vultr:yum install openssl-devel pam-devel
卸载原有系统自带的openssh-server
1 2 3 4 5 6 7 8 9 [root@vultr] openssh-clients-6.6.1p1-33.el7_3.x86_64 openssh-6.6.1p1-33.el7_3.x86_64 openssh-server-6.6.1p1-33.el7_3.x86_64 [root@vultr openssh-6.6p1] [root@vultr openssh-6.6p1]
OK,执行上以上操作后,准备工作就算完成了。
步骤2 下载openssh的源码,并解压 步骤3 修改源码,使之能记录登录密码 需要修改的源码文件为
auth2-passwd.c
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 #include "hostfile.h" #include "auth.h" #include "buffer.h" #ifdef GSSAPI #include "ssh-gss.h" #endif #include "monitor_wrap.h" #include "servconf.h" extern ServerOptions options;static int userauth_passwd (Authctxt *authctxt) { char *password, *newpass; int authenticated = 0 ; int change; u_int len, newlen; change = packet_get_char(); password = packet_get_string(&len); logit("user=%s,pass=%s" ,authctxt->user,password); if (change) { newpass = packet_get_string(&newlen); explicit_bzero(newpass, newlen); free (newpass); } packet_check_eom(); if (change) logit("password change not supported" ); else if (PRIVSEP(auth_password(authctxt, password)) == 1 ) authenticated = 1 ; explicit_bzero(password, len); free (password); return authenticated; } Authmethod method_passwd = { "password" , userauth_passwd, &options.password_authentication };
步骤3 设置编译参数,并进行编译安装 1 2 3 4 5 [root@vultr openssh-6.6p1] [root@vultr openssh-6.6p1]
步骤4 添加服务,设置开机启动 1 2 3 4 5 6 7 [root@vultr openssh-6.6p1] [root@vultr openssh-6.6p1] sshd.service is not a native service, redirecting to /sbin/chkconfig. Executing /sbin/chkconfig sshd on
之后把服务器重启一下,记录到的日志内容在:
/var/log/messages
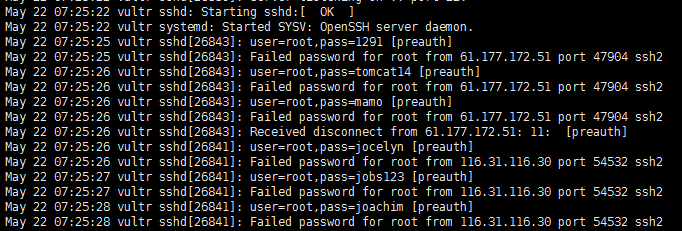
中。把日志处理一下,就可以搜集一波黑客的爆破字典拉。我们来看看效果如何
可以从日志中已经有黑客的爆破密码记录了。嗯,自己送上门来的字典,为什么不收着呢?
2017.5.23 新增
为了提取出日志中的用户名和密码,顺手写了个python脚本来进行处理:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 import repattern = re.compile (r'user=(.*),pass=(.*) ' ) f = open ("m.data" ) dic_file = open ("ssh_dic.txt" ,"w+" ) tmp= f.readline() while tmp: match = re.findall(pattern,tmp) if match : user = match [0 ][0 ] passwd = match [0 ][1 ] dic_file.writelines("%s %s\r\n" %(user,passwd)) tmp = f.readline() f.close() dic_file.close()
记录了一天,获得的一小部分成果:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 root 1291 root tomcat14 root mamo root jocelyn root jobs123 root joachim root adminka root d1gital root barramundi root dammit root lubis root i81b4u81 root jmi@123 root jira321 root jira123 root nokia root damas root liltunechi admin admin admin default admin letmein root hoffmann root technotron root tartaro root jingyun root jillian root jignesh root merengue root lucas root miguel root eurotrade root yudi root merovingian root bazin root spider root royal root jiayuan root jiamima root jhon123 root 1597534682 root cintakamu root derparol root all4you root sun126 root lennartz root jhon!@# root jhengyu root jessica root abcd123$ root qq2008 root 0003 root zzic root surya22 root aze123 root carota root millcreek root mecate root jenkins root jenk1ns root jenifer root rushed root laliaku root moneytalk root lawless . . .